For a business owner, the security of their business should make it to the top of your priority list. As per Microsoft, the current technological advancements have developed notorious tools that can be used to steal passwords, often intended to harm businesses. Data breaches and cyberattacks are more common than ever, as owners globally are taking their business to digital platforms for more sales exposure and profitability. However, that doesn’t mean such attacks can’t be prevented or fought the right way. With increased threat, the fortifying of network infrastructure can be the maker or breaker of your business.
Microsoft also adds that even strong passwords and Multi-Factor Authentication are often ineffective since they often get reused, saved on a server accessible to many others, and lack any biometric authentication process to keep your data protected. This is where SSH or the Secure Shell comes in. SSH is a key-based authentication that comprises a key pair (access credential) based on the Public Key Interface technology known to be one of the most effective methods of data authentication and encryption. Since SSH protocol is widely used for cloud/network environments, the best part about these is they can be easily verified and gain access control. But how does it replace passwords? Let’s dig a little deeper.
What exactly is SSH?
Credits: Manage Engine
A network protocol developed in 1995 by Tatu Ylönen, SSH on the higher level, with its public-key-based authentication has similar functionality as passwords, however, it also encrypts all connections between two endpoints of the network. This way it replaces all insecure file transfer and login protocols such as FTP, rlogin, etc. Because of its individuality and strong encryption SSH is primarily used by network admins to deploy software patches, run commands, and transfer files in a system remotely. Furthermore, SSH keys are also automation enablers of connected processes, promote Single-Sign-On (SSO), and manage many other digital identity management protocols – making it an excellent tool for businesses today.
Why use SSH keys instead of Passwords?
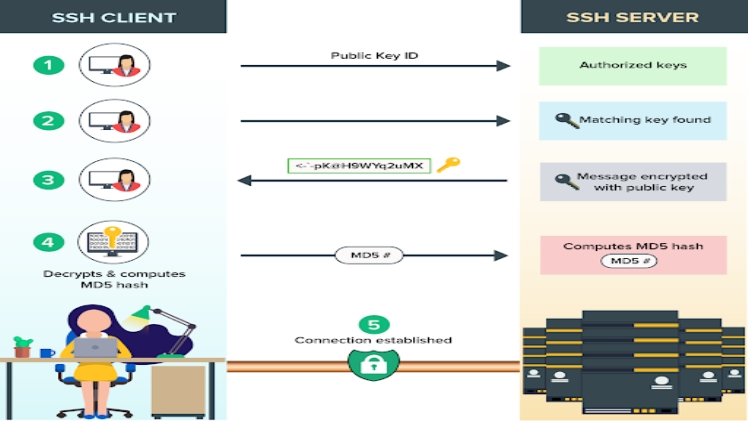
SSH protocols are built into the UNIX and LINUX servers for establishing protected connections between the SSH client and server. In its setup process, the SSH client begins the connection protocol, it accesses the public-key cryptography, for authenticating the identity of the SSH server. However, proceeding to the initial stage, the SSH protocol can now apply symmetric encryption, hashing algorithms for fortifying the privacy of the data now exchanged between both sides of the SSH.
Businesses that still rely on traditional passwords for client verification often ignore the potential risks that can come from doing so. The SSH keys, on the other hand, generate a public-private key pair with the respective SSH client, in an ssh-keygen command. This way, the user now safely keeps their authorized key (private key) into the respective server file for the connection to take place. Now, while trying to log in remotely, the SSH server searches authorized_keys, which the user can verify with the server by its respective private key from the pair. Some of the use cases of such a system would be when a user tries to securely access resources from the server on remote, etc. In case of fallout, here’s how SSH keys stay secured:
- The Public Key Interface’s strong cryptographic and verification processes
- More user-friendly as SSH keys establish an automated connection between users and servers, so there’s no scope for manual inputs of passwords.
- The algorithms used in the SSH keys often apply computation methods to generate random combinations of numerals of distinct lengths that cannot be taken advantage of forcibly in any reasonable amount of time.
Conclusion
SSH protocols are known as a universal way to manage systems, however, when left unchecked the untracked SSH keys can be the access points to hackers or data leaks. To prevent any such possibilities of SSH Key Abuse, end-to-end visibility of all SSH keys should be maintained closely – since it can bring out any key that the attacker may try to insert their own SSH keys.
Unlike popular belief, understanding the functionalities of SSH keys is simple and easy, and can be extended to business solutions. In case you’re an IT professional yourself, looking for fulfilling, new job opportunities, here are some of our recommendations to get started:
Upwork
Perfect for freelancers and solopreneurs, the platform connects many businesses to professionals globally. With transparent ways to connect, workout agreements, and flexible payments, Upwork is a great place to get your feet wet if you’re looking to establish a career as a freelance software developer.
CodeClouds
With a team of 400+ experienced professionals across the world, folks here have been in the industry for a decade and counting and with solid market understanding. They’re currently having numerous remote openings for project managers, software developers, etc, so if you’re looking for web developer jobs, they can be an excellent place to collaborate and learn.
Satrix Technologies, Lucknow
Folks here specialize in delivering web and mobile app development along with graphics design. Their expertise includes Magento custom web application development, android app development, and many more. They’re currently hiring web developer freshers, among many other open positions.

